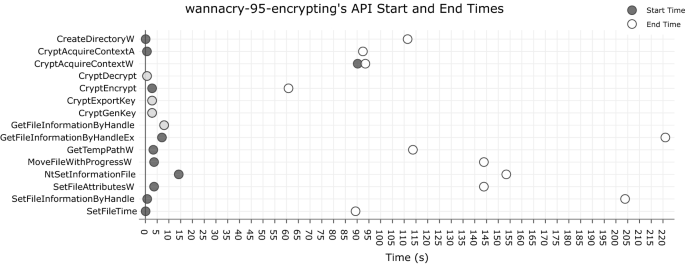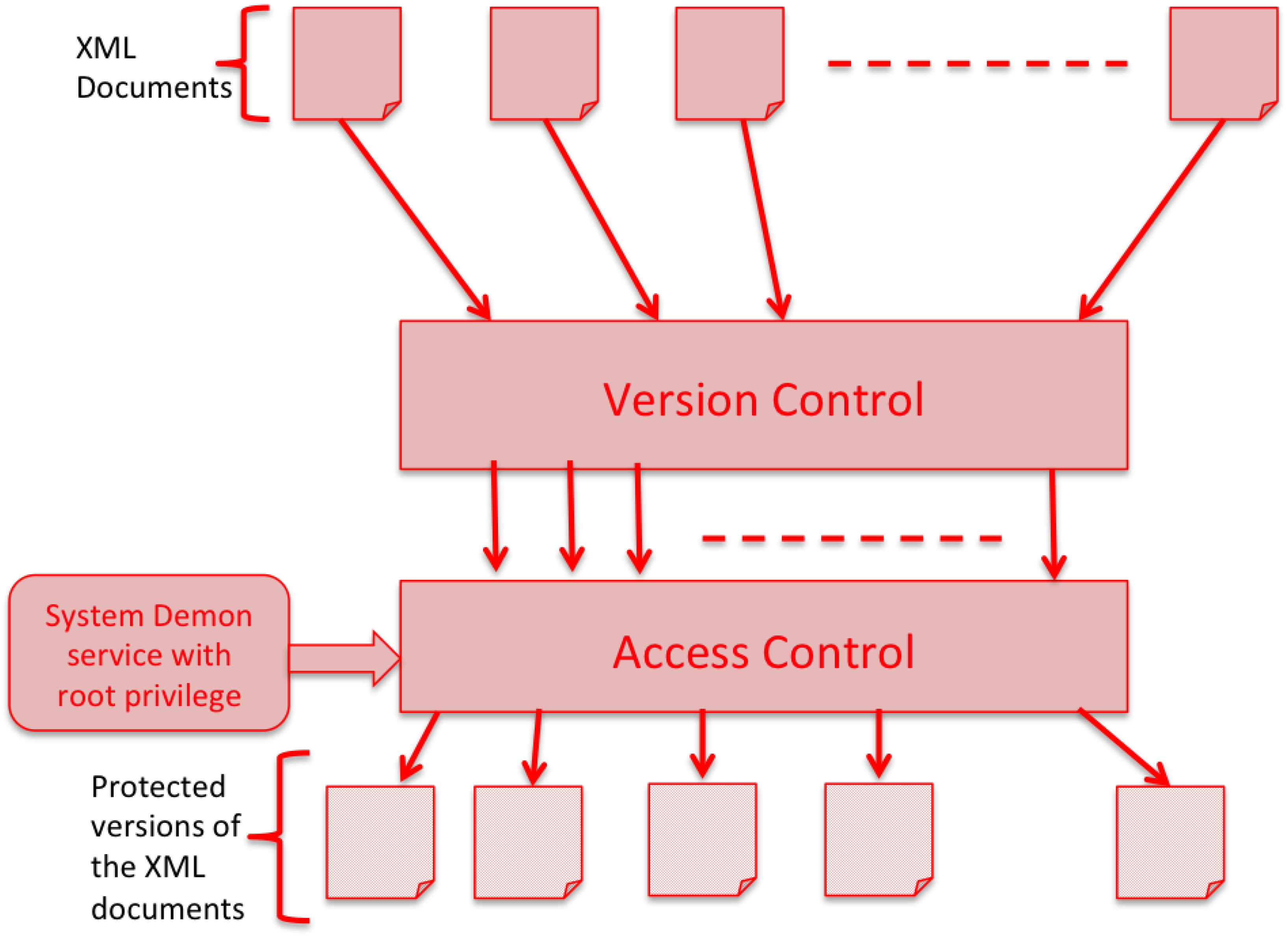
Applied Sciences | Free Full-Text | Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack

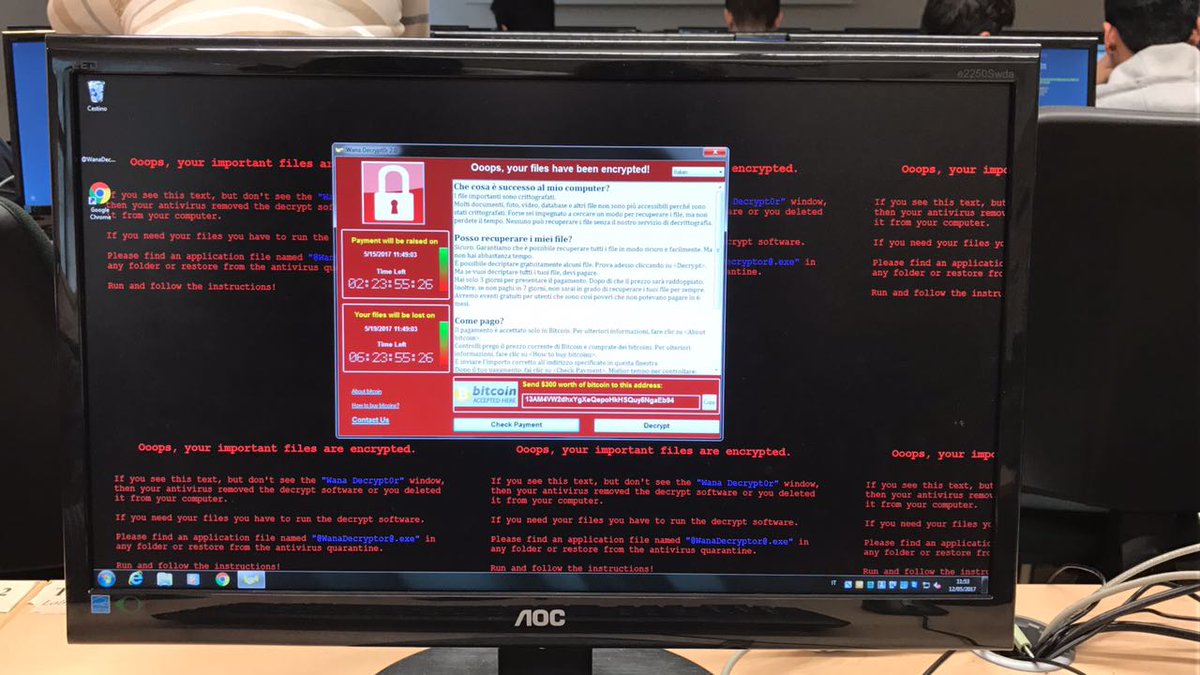
Cyber-Physical Attacks and the Value of Healthcare Data: Facing an Era of Cyber Extortion and Organised Crime | SpringerLink